How to integrate a new proxy into your code?
How to integrate a new proxy into your code?
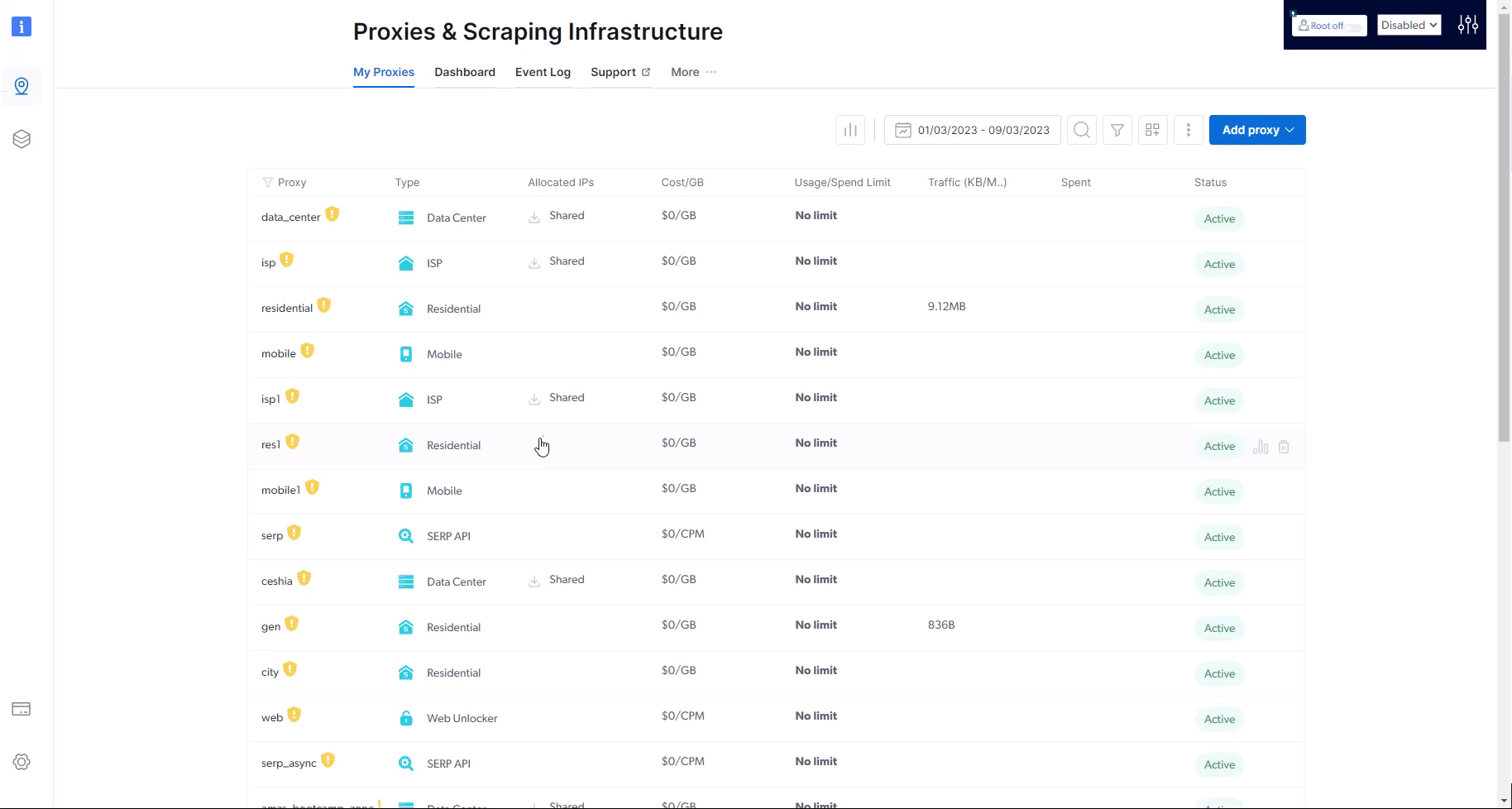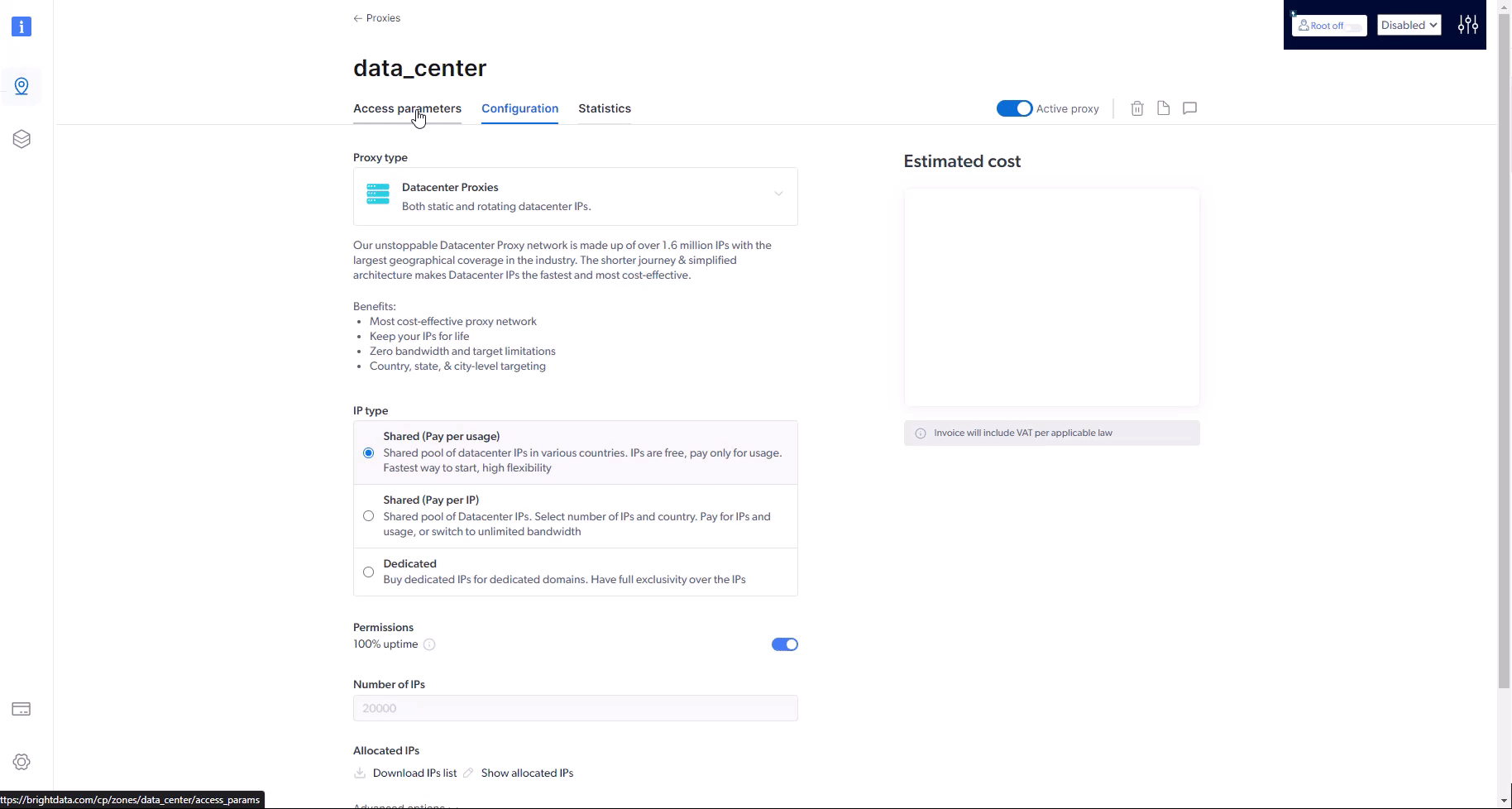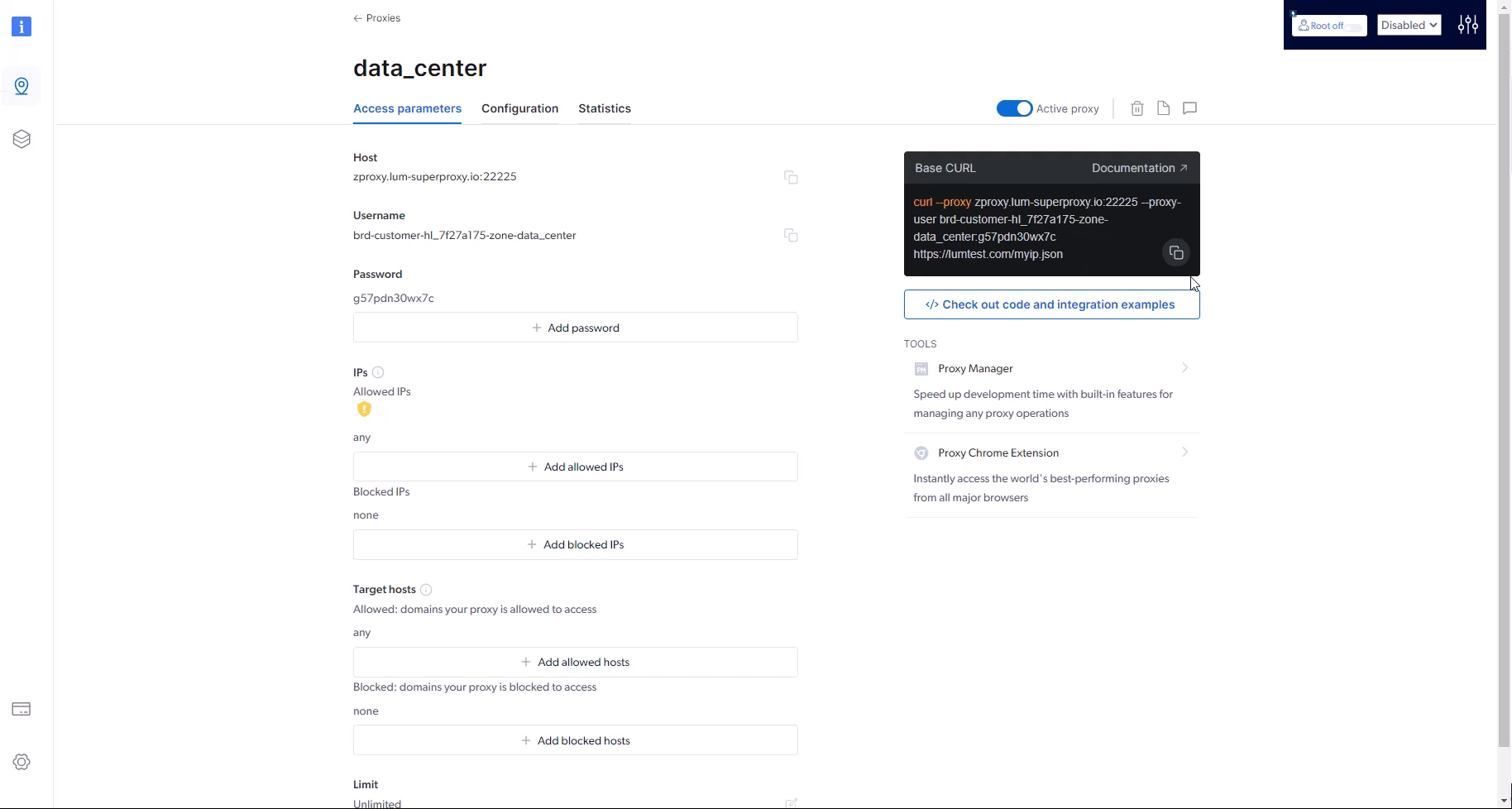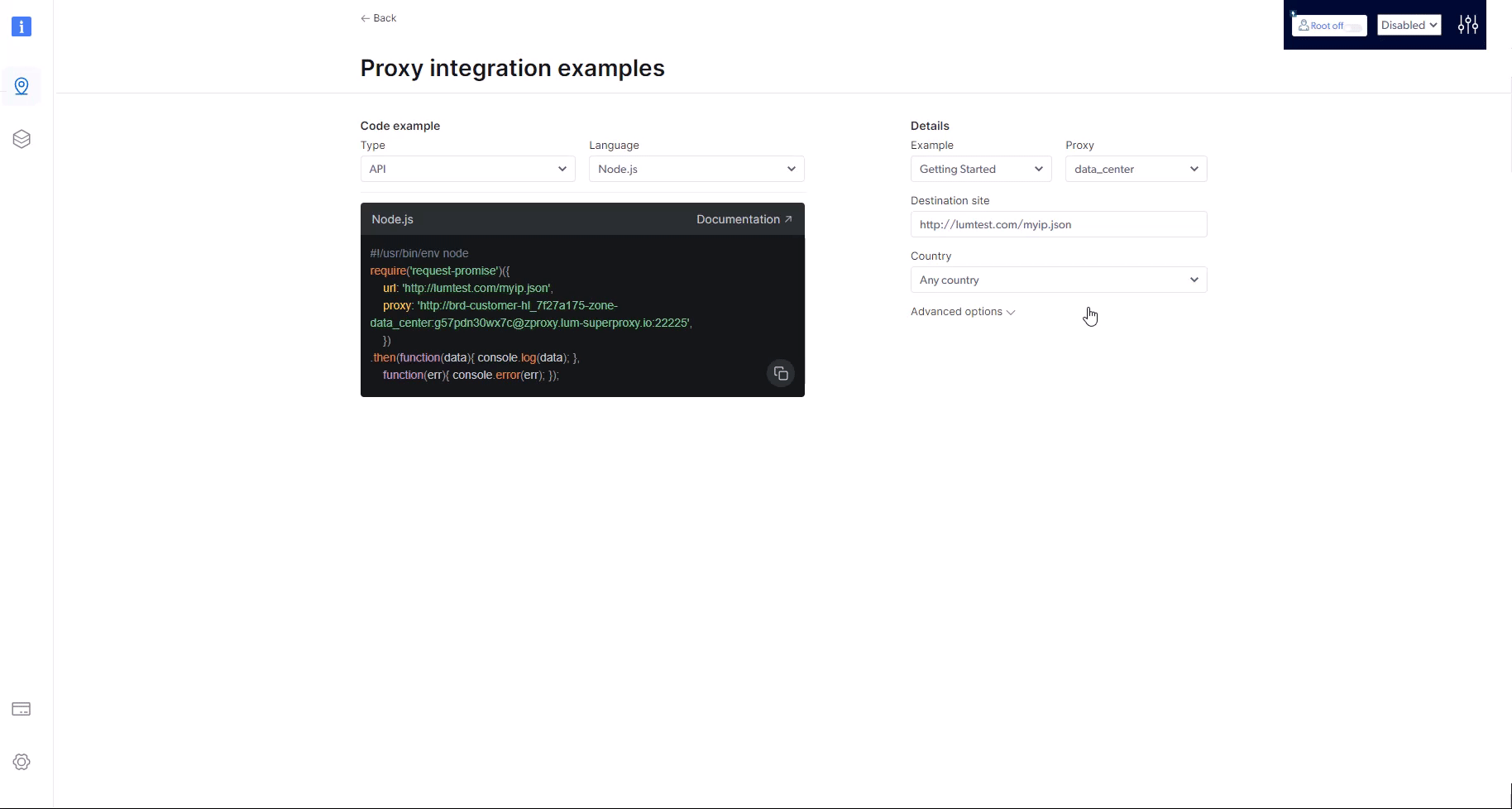
How to integrate a proxy into 3rd party software?
How to integrate a proxy into 3rd party software?
How to target a Specific Country?
How to target a Specific Country?
-country flag, after your zone’s name in the request, followed by the 2-letter ISO code for that country.In the example below: We added -country-us to our request, so we will send a request originating from the United States (“us”).How to target the EU region
How to target the EU region
How to target a Specific City?
How to target a Specific City?
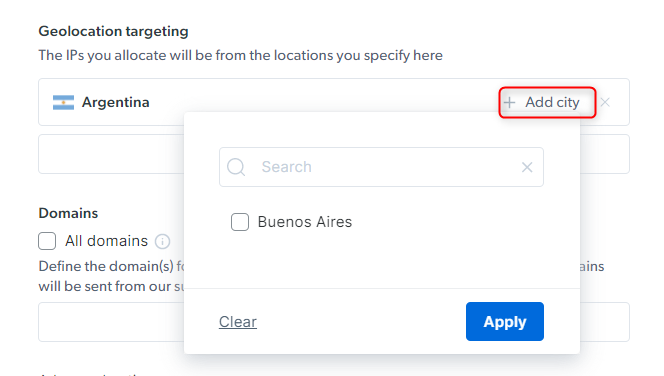
-country-ar-city-buenosairesWhere does Bright Data have proxies?
Where does Bright Data have proxies?
- Iran
- Iraq
- Syria
- Lebanon
- Palestine
- North Korea
- Cuba
- Sudan
- Crimea region of Russia
How to view the proxy event log?
How to view the proxy event log?
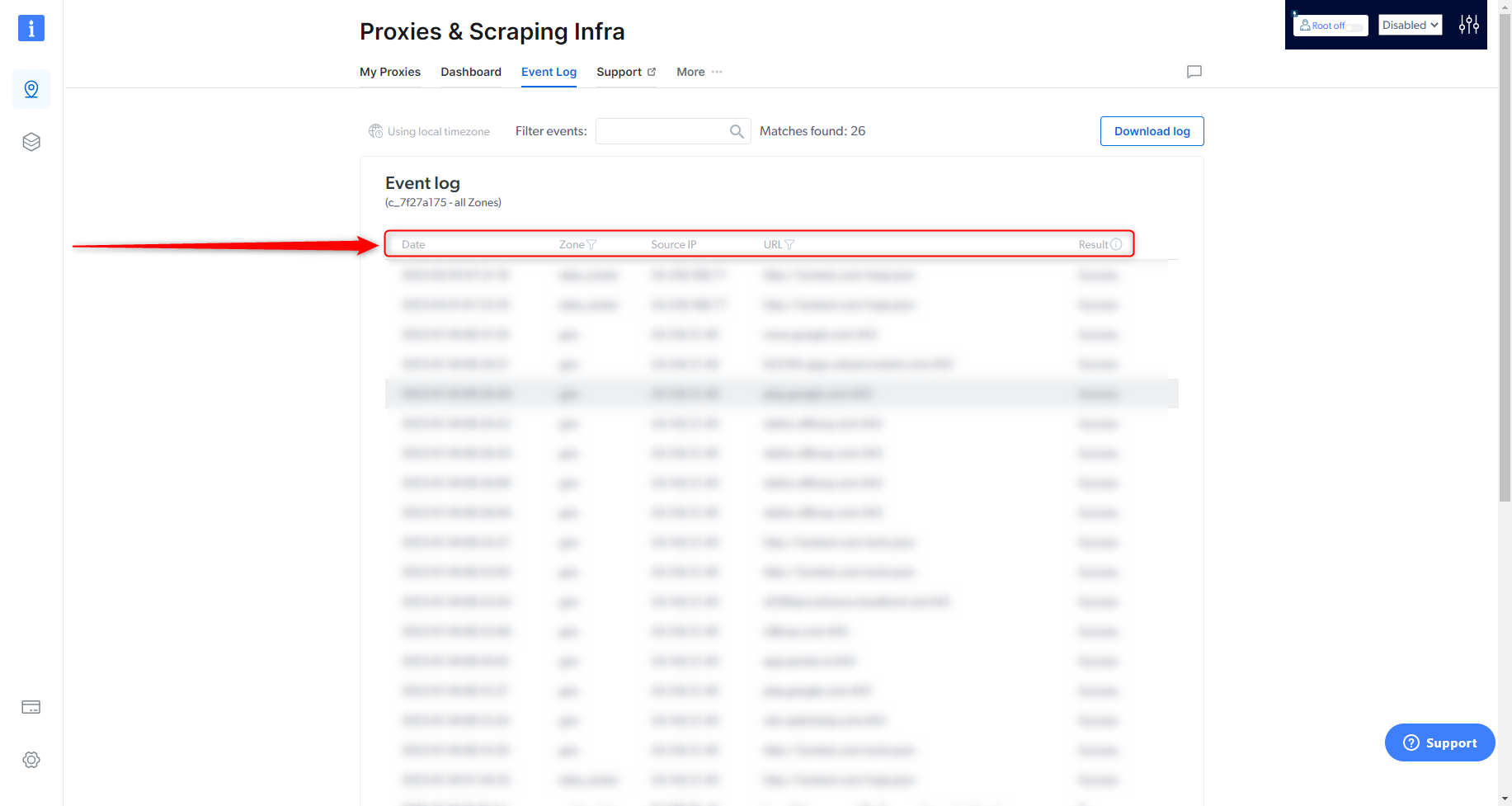
- Date: Time and date of the request
- Zone: What Zone was used for the request
- Source IP: What IP the request was made from
- URL: The target site of the request
-
Result: Success or Fail of the request
How to keep using the same IP in multiple requests?
How to keep using the same IP in multiple requests?
- This can be done by adding the
sessionparameter to the proxy username:
- Session ID can be any random string/counter: requests with the same session string will use the same Proxy Peer (as long as possible); requests with different session strings will be assigned different Proxy Peers.
- To force an IP change, just modify the session ID
- If an assigned Proxy Peer (exit node IP) becomes unavailable, the Super Proxy will return an error “502 - No peers available” for the first request and then on the second request the super proxy will assign a new peer even if you do not change the session ID.
- The Session IP is kept persistent for up to 5 minute of idle time. After 5 minutes with no requests, the IP is released back to the pool. To keep this Session/IP for longer, send a tiny keep-alive request every 30 seconds, to prevent this session from becoming idle for over a minute. This request may be anything small, such as /favicon.ico, or even a request that returns 404 (as long as the web server does not disconnect the socket due to this request).
How to target specific OS?
How to target specific OS?
How to use a specific IP?
How to use a specific IP?
- Send a test request with a ‘—verbose’ or ‘-v’ option added (this will turn on verbose logging)
-
Locate the x-brd-ip response header and copy its value
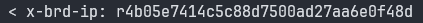
- Add the -ip- flag to your request, after your zone’s name and use the hashed IP value copied in the previous step
- Send a test request, and review the response
How to targeting an ASN specific IP?
How to targeting an ASN specific IP?
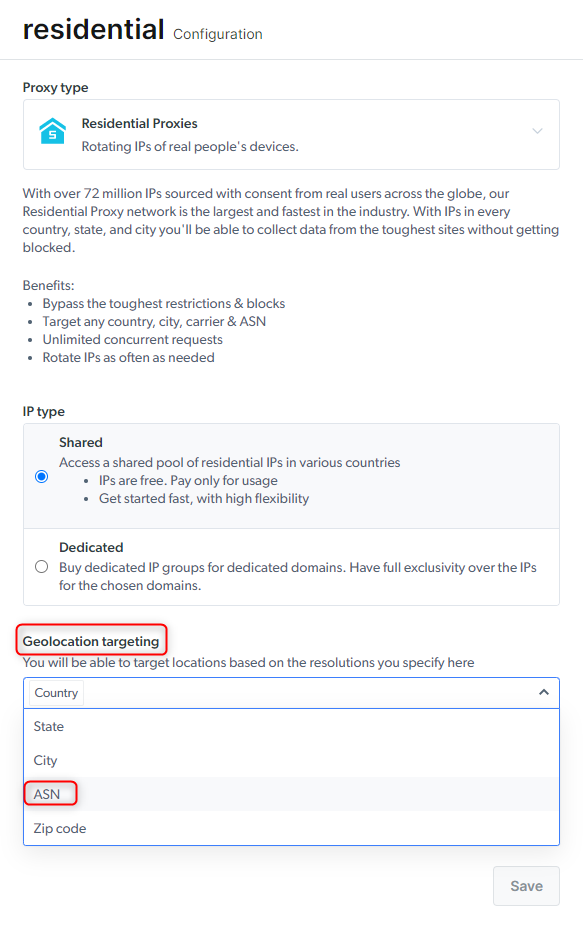
and be integrated when using the Residential proxies. For example:
How to target residential proxy using group IP (gIPs)?
How to target residential proxy using group IP (gIPs)?
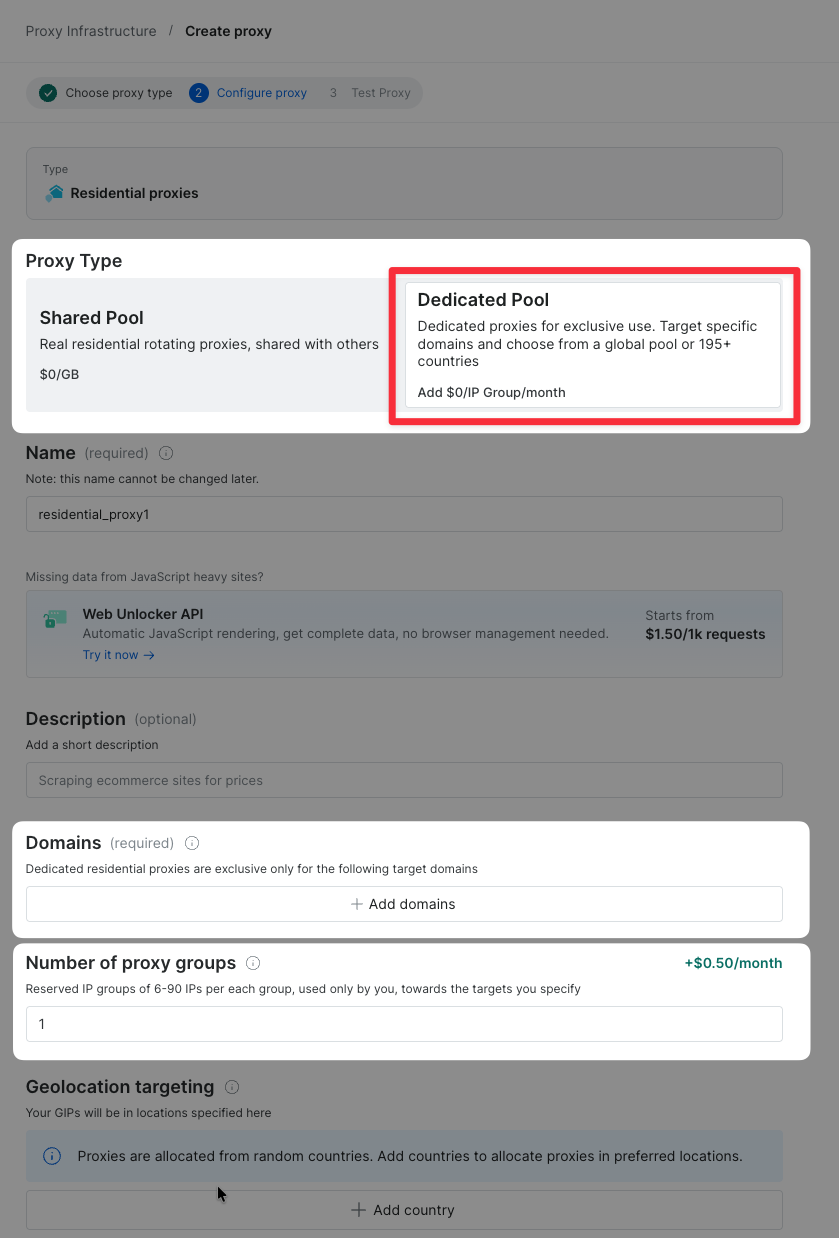
How to browse Chinese sites by using Chinese Residentials IPs
How to browse Chinese sites by using Chinese Residentials IPs
Targeting Chinese Residential IP peers is enough:
Carrier-specific Proxy peer IP
Carrier-specific Proxy peer IP
- You can choose to use a specific carrier from this list:
- For Example
Which Bright Data products are best for scraping search engines (SERPs)?
Which Bright Data products are best for scraping search engines (SERPs)?
For single-step scraping:
SERP API is the ideal product for targeting SERPs as it has a guaranteed success rate (pay only for success) with active unlocking, automatically chooses the best proxies, customizes headers, fingerprinting, solves CAPTCHAs, and more.For multi-step scraping (playwright/puppeteer/selenium):
Browser API is the ideal product as it is our fully cloud-hosted browser designed to help you easily focus on your multi-step data collection while we take care of the full proxy and unblocking infrastructure for you, including CAPTCHA solving.Can I target Google SERPs from the Residential, Datacenter, or ISP Proxy network?
Can I target Google SERPs from the Residential, Datacenter, or ISP Proxy network?
Targeting search engines via bright data Residential & Mobile networks
Targeting search engines via bright data Residential & Mobile networks
How can I see the IP address of my Residential proxy?
How can I see the IP address of my Residential proxy?
x-brd-ip . This reply header includes a unique hash which represents the IP address you used for this request.